February 10, 2026
at
9:20 am
EST
MIN READ
Zero-Knowledge Proofs: How Transformational Can They Be?

In the evolving landscape of cryptography and blockchain, few innovations have sparked as much excitement as zero-knowledge (ZK) proofs. Once an obscure academic concept buried in theoretical computer science papers, ZK proofs have rapidly moved from whiteboards to mainnet, becoming a cornerstone of the next generation of crypto infrastructure.
At their heart, ZK proofs challenge a long-held assumption in digital systems: that verification requires exposure. Whether logging into an app, proving your identity, or confirming a transaction, we’ve always had to reveal something to be trusted. ZK technology breaks that trade-off, allowing us to prove facts, about identity, data, or computation, without disclosing the underlying information.
Beyond privacy, it enables scalability, interoperability, and trustless verification on a global scale. From ZK rollups that expand blockchain throughput to privacy-preserving identity and compliance systems, zero-knowledge proofs are redefining what is possible in crypto.
Summary
- Zero-knowledge (ZK) proofs enable verification of information such as identity, balance, or transaction validity without revealing underlying data
- Though first conceived in the 1980s, ZK technology only became practical recently due to advances in computation, cryptography, and blockchain adoption
- ZK proofs power private transactions, decentralized identity, DAO voting, and cross-chain interoperability, while scaling Ethereum through ZK rollups that bundle thousands of transactions into a single proof
- Though computationally demanding, ZK rollups offer instant finality, lower fees, and strong security, placing them ahead of Optimistic counterparts
What is a Zero Knowledge Proof?
A zero-knowledge (ZK) proof is a cryptographic method that enables one party (the prover) to convince another (the verifier) that a statement is true, without revealing why it’s true or any extra information.
For example, Alice wants to prove to Bob that she knows the password to a hidden door inside a cave, without telling him the password itself. She enters the cave, opens the door, and reappears on the other side. Bob can’t see how she did it, but he knows she must have known the password.
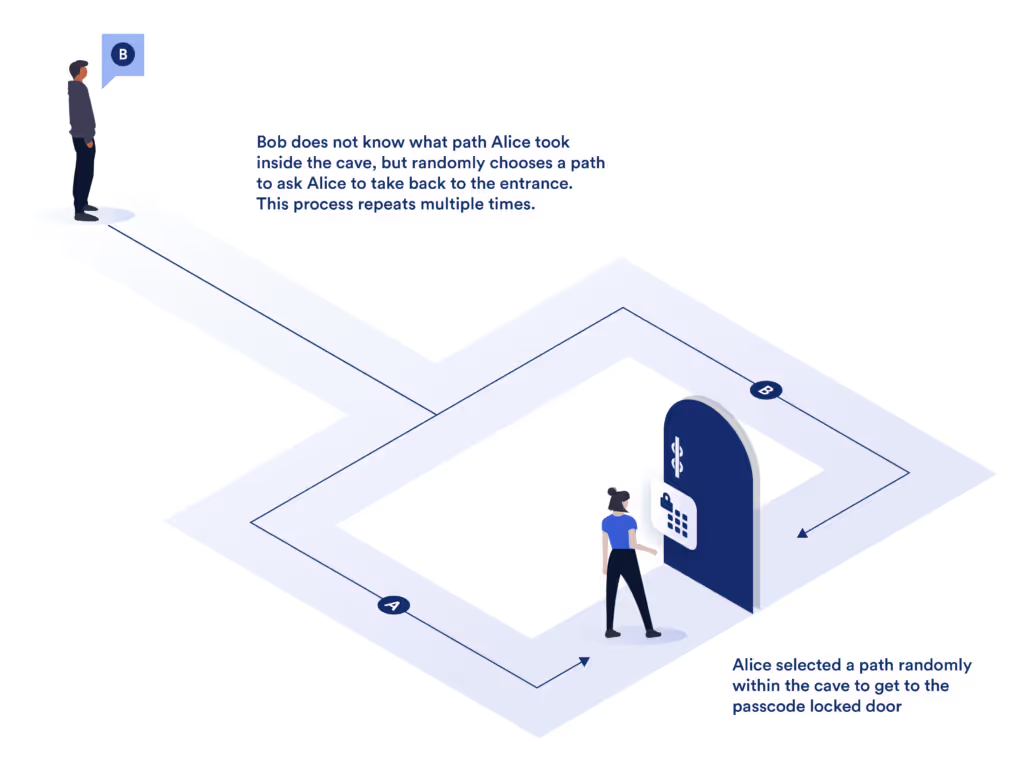
Traditionally, verification required revealing some information: an ID, password, or data. ZK proofs invert that paradigm, enabling one to prove identity, authenticity, or ownership without exposing the data itself.
In digital systems, this means you can:
- Prove you’re over 18 without revealing your birth date
- Prove sufficient funds without disclosing your wallet balance
- Prove a transaction’s validity without exposing its contents
This “prove without revealing” capability is foundational to privacy-preserving systems that remain secure and transparent, two qualities ZK proofs uniquely reconcile.
How Do They Work?
Zero-knowledge proofs rely on deep mathematical structures and cryptographic primitives, but conceptually, they boil down to three essential properties:
- Completeness: If the statement is true, an honest prover can convince the verifier that it’s true.
- Soundness: If the statement is false, no cheating prover can convince the verifier otherwise.
- Zero-Knowledge: The verifier learns nothing beyond the fact that the statement is true.
In practice, there are several families of ZK proofs, but two major ones dominate current discussions: Interactive and Non-Interactive ZK proofs.
In early designs, zero-knowledge proofs were interactive. The prover and verifier engaged in a back-and-forth conversation where the verifier sent random challenges, and the prover responded with proofs that collectively built confidence in the truth of a statement. Although this model works well in theory, it is not efficient enough for blockchain environments where parties are often unable to easily interact in real time.
To make things practical, cryptographers developed non-interactive zero-knowledge proofs (NIZKs), which are proofs that require only a single message from prover to verifier. The most famous of these is the zk-SNARKs, which allows for extremely compact proofs that can be verified in milliseconds. Another variant is zk-STARKs, which remove the need for a trusted setup and offer post-quantum security.
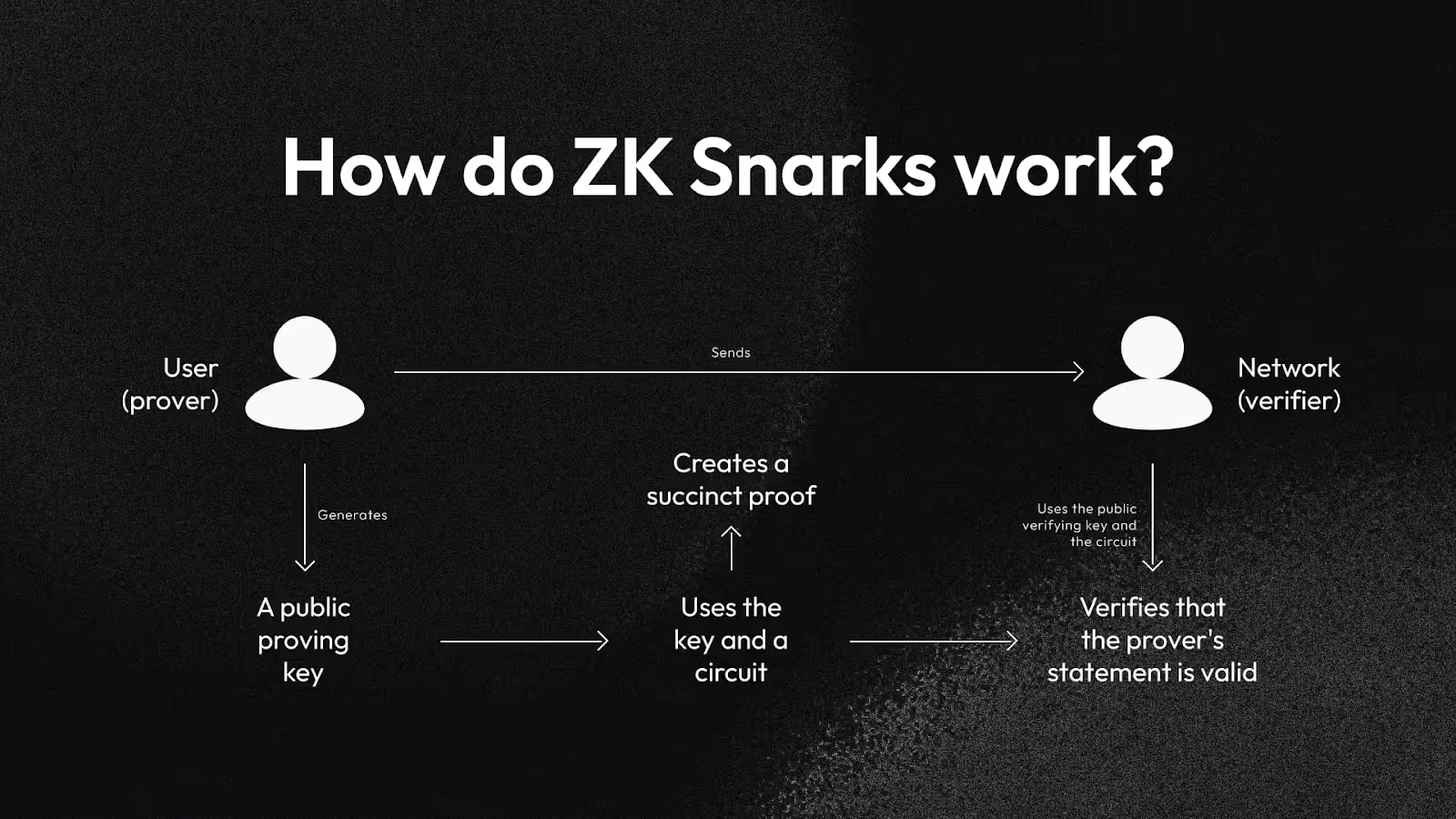
In essence, these systems allow a prover to generate a mathematical “fingerprint” of a valid computation. The verifier can then check that fingerprint without re-doing the entire computation themselves. This is what makes them so powerful in blockchain scaling, where thousands of transactions can be verified quickly and cheaply by checking a single cryptographic proof.
When Were Zero Knowledge Proofs Invented?
Zero-knowledge proofs date back to the mid-1980s, when researchers Shafi Goldwasser, Silvio Micali, and Charles Rackoff introduced the concept in their groundbreaking paper, “The Knowledge Complexity of Interactive Proof Systems” (1985).
Their early theoretical models laid the groundwork for decades of cryptographic innovation, but it wasn’t until the 2010s, thanks to advances in computational efficiency and the rise of blockchain technology, that ZK proofs became practical.
Projects like Zcash, which launched in 2016, were among the first to deploy zero-knowledge proofs at scale, using zk-SNARKs to enable private transactions on a public ledger. Since then, ZK proofs have evolved dramatically, with better efficiency, faster proof generation, and new frameworks (like zk-STARKs, Halo, and PLONK) making them more accessible for developers and scalable for real-world systems.
What are ZK Proof Applications in Crypto?
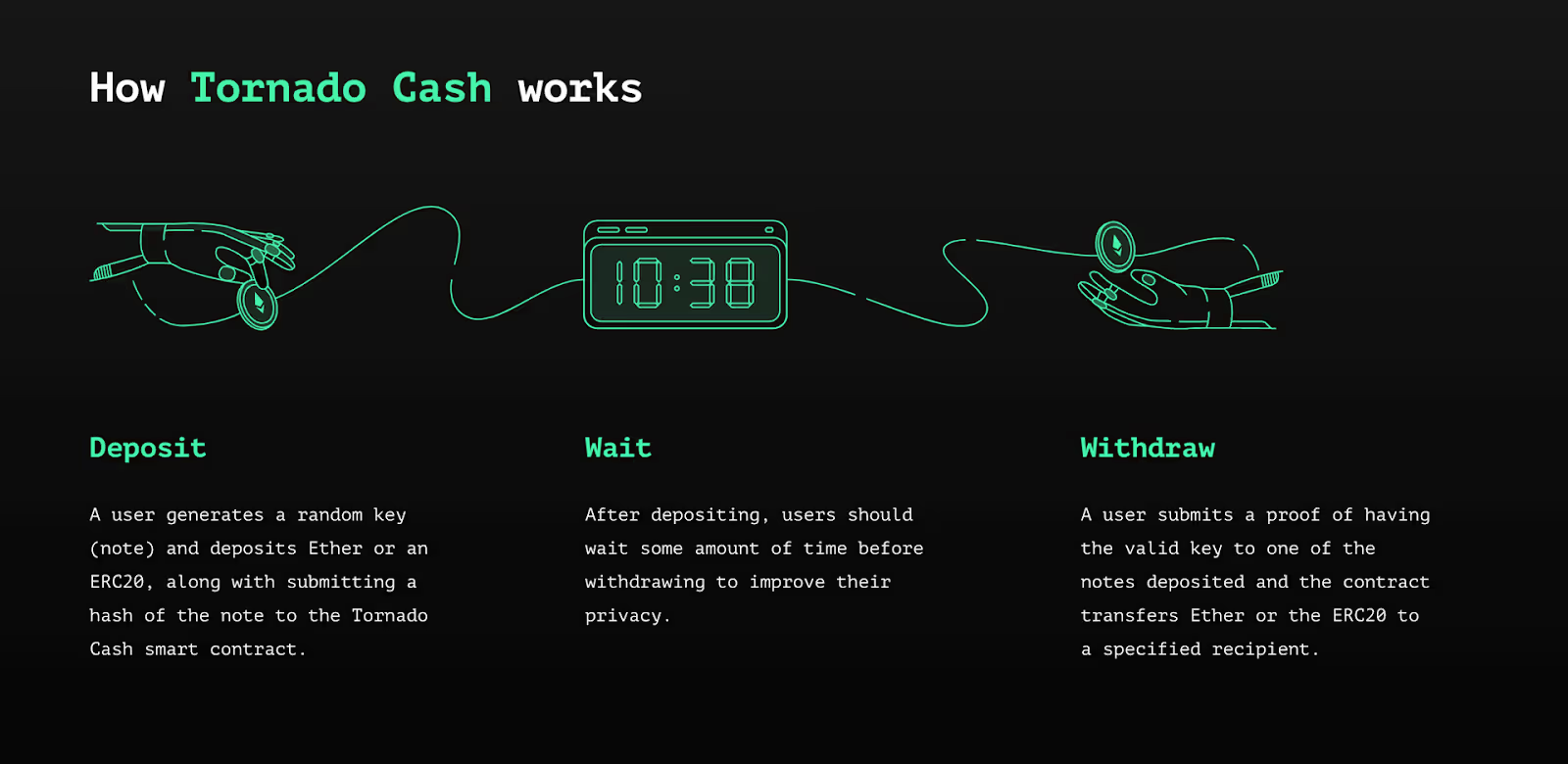
The most intuitive and well-known use case is privacy-preserving transactions. Zero-knowledge proofs allow users to transact on a public blockchain without exposing sensitive information such as transaction amounts or counterparties. The pioneering example is Zcash, which introduced shielded transactions that protect user privacy while maintaining verifiable integrity on-chain. Building on this foundation, projects like Tornado Cash, Aztec and Railgun have extended ZK technology to Ethereum, enabling private smart contract interactions and confidential DeFi transactions.
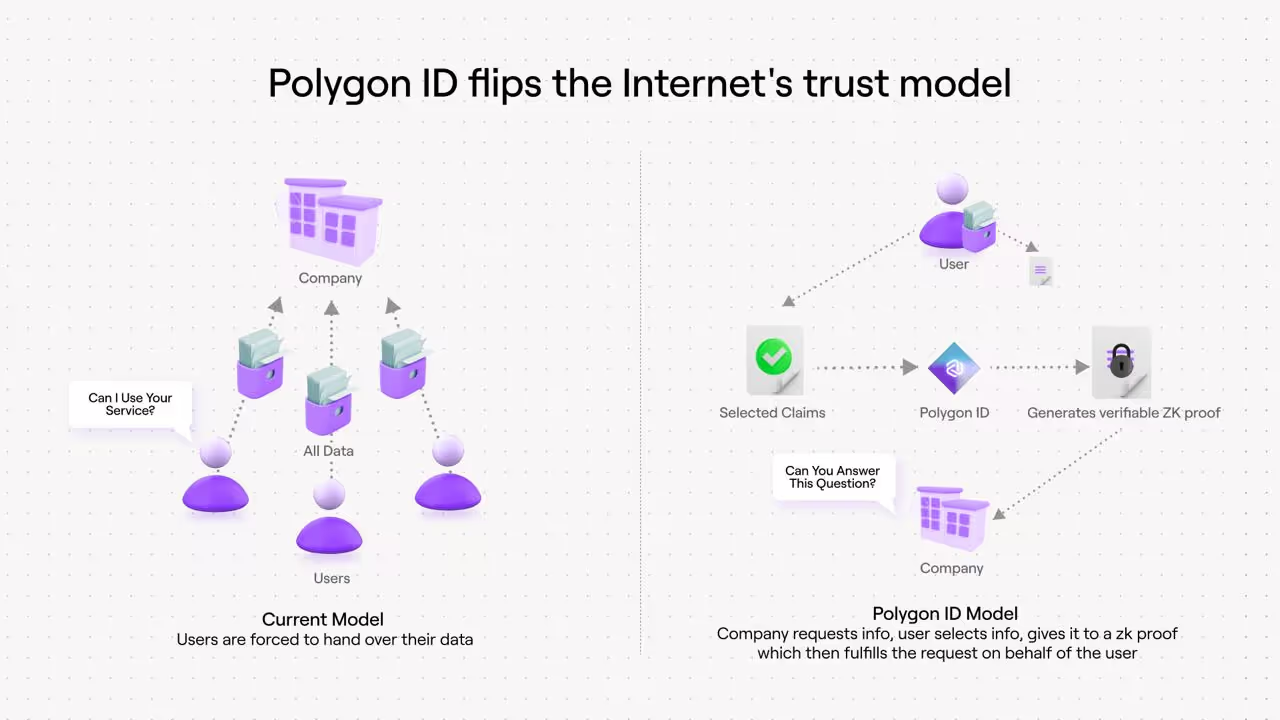
Beyond privacy, zero-knowledge proofs are revolutionizing digital identity and regulatory compliance. They enable selective disclosure, the ability to prove specific facts about oneself without exposing personal data. For instance, a user can prove they are KYC-verified without revealing their name, or confirm that they are not on a sanctions list without sharing identifying details. This principle underpins emerging ZK identity systems such as Worldcoin’s Proof of Personhood, Polygon ID, and zkPass.
ZK proofs also offer powerful applications in voting and governance. Within decentralized autonomous organizations (DAOs), they can facilitate anonymous yet verifiable voting processes, ensuring that outcomes are transparent while individual voter identities remain private. This helps reduce the risk of coercion or retaliation and encourages more honest participation in collective decision-making, strengthening the democratic principles of decentralized governance.
Another area where ZK proofs are beginning to shine is cross-chain verification. In a multi-chain world, establishing trust between separate blockchains has traditionally required intermediaries or complex bridging mechanisms. Zero-knowledge proofs provide a more elegant solution: a proof generated on one chain can attest to the validity of its state, which another chain can independently verify. This enables trustless interoperability, allowing different blockchains to communicate securely without relying on centralized validators.
ZK technology is also being harnessed to improve Ethereum’s scalability through ZK rollups. By bundling thousands of transactions into a single cryptographic proof, these rollups dramatically reduce on-chain data load while preserving security. The result is faster, cheaper, and more efficient transaction processing, laying the groundwork for Ethereum to handle mass adoption without compromising its decentralization.
ZK Rollups Explained
Among all applications enabled by ZK proofs, ZK rollups are arguably some of the most transformative. They address one of the biggest challenges in crypto: blockchain scalability.
Since the beginning of blockchain technology, all blockchains were subject to the blockchain trilemma: a concept which stated that all blockchains could only achieve two of the three core properties: security, scalability and decentralization. Blockchains like Ethereum are secure and decentralized but remain slow and expensive. Every transaction must be verified by every node, creating a bottleneck that limits throughput and drives up gas fees, heavily reducing the accessibility of the chain.
A rollup is a Layer-2 solution that executes transactions off-chain, then posts a summary back to the main chain or the Layer-1, in most cases, Ethereum. There are two main types of rollups, Optimistic rollups and ZK rollups.
In a ZK rollup, hundreds or thousands of off-chain transactions are batched together. A prover generates a ZK proof, specifically known as a validity proof, showing that all batched transactions adhered to the rules of the blockchain. That single proof is then submitted to the main chain, which can verify it quickly and conclusively.
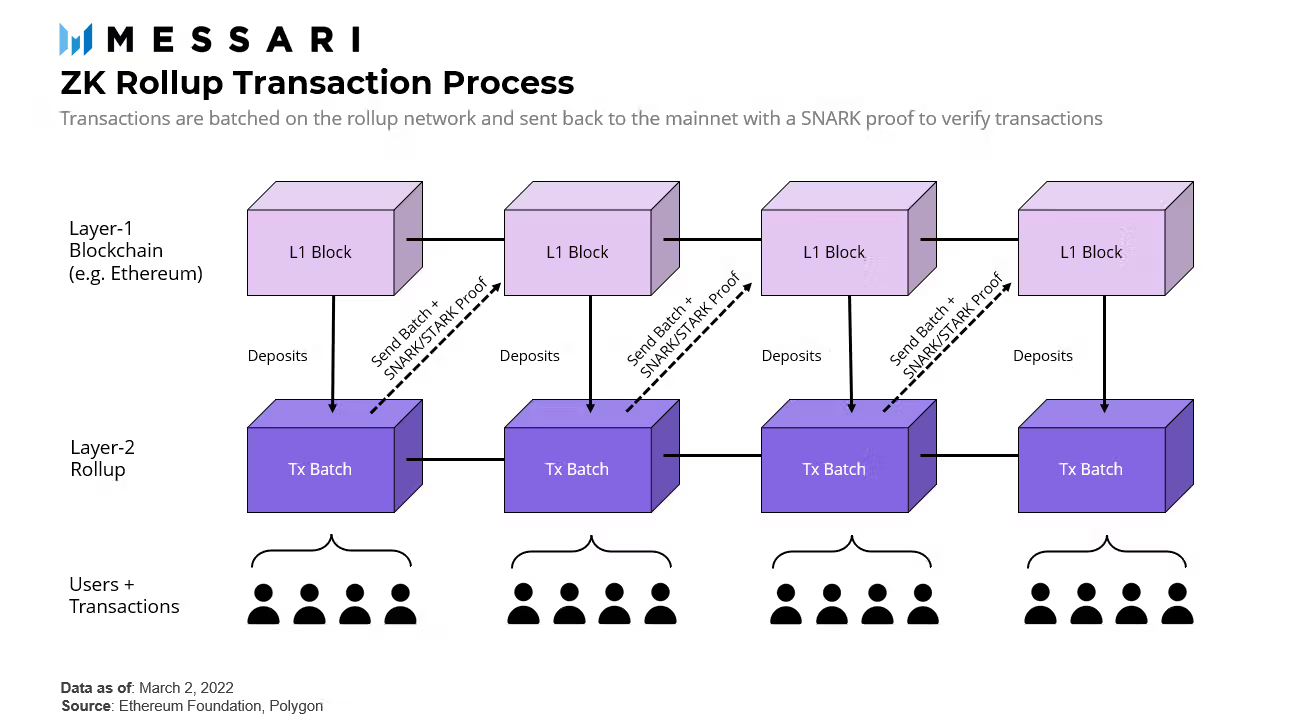
This design dramatically reduces data and computation on Layer-1, while maintaining the same security guarantees as if every transaction were processed individually, removing speed and scale bottlenecks on the Layer-1.
Some examples of ZK rollups include:
- zkSync Era: Developed by Matter Labs, uses zk-SNARKs for fast finality
- StarkNet: Built on zk-STARKs, emphasizing scalability and transparency
- Polygon zkEVM: A zero-knowledge implementation of Ethereum’s Virtual Machine (EVM), enabling compatibility with existing smart contracts on Ethereum
- Lighter: A perpetual DEX platform built on a custom ZK rollup using zk-SNARKs, specifically Plonky2
Benefits of ZK Rollups
By compressing thousands of transactions into a single cryptographic proof, ZK rollups dramatically increase throughput, enabling blockchains like Ethereum to process far more activity without sacrificing decentralization or security.
Security is another key strength. Unlike Optimistic rollups, which rely on economic incentives and week-long challenge periods to detect fraud, ZK rollups use mathematical validity proofs to guarantee correctness upfront. Once a proof is verified on-chain, the underlying transactions are final and immutable, eliminating delays and uncertainty.
This also translates into faster confirmation times. Transactions within a ZK rollup are effectively settled the moment their corresponding proof is validated, giving users near-instant finality compared to the waiting periods common in Optimistic systems.
Cost efficiency is another major benefit. Because ZK rollups post only minimal data to the Layer-1 blockchain, gas fees are significantly reduced, making it more affordable for users and applications to operate on Ethereum.
Perhaps most intriguingly, ZK rollups open the door to enhanced privacy. Since they are built on zero-knowledge cryptography, it’s theoretically possible to embed confidentiality directly into the rollup itself, allowing for private yet verifiable transactions at scale.
The main limitation today lies in computational demand. Generating zero-knowledge proofs is still resource-intensive, requiring powerful hardware and advanced cryptographic techniques. However, ongoing progress, particularly in hardware acceleration, circuit design, and recursive proofs, is steadily reducing these costs, making ZK rollups more efficient with each generation.
Comparison With Optimistic Rollups
Optimistic rollups, such as Arbitrum and Optimism, follow a different philosophy. They operate under the assumption that all off-chain transactions are valid by default. Only when someone challenges this assumption does the system require a “fraud proof” to verify the dispute, a process that typically takes about a week. This model works well in practice but introduces latency in transaction finality and depends on participants being incentivized to detect and report invalid activity.
With ZK rollups, each batch of transactions is accompanied by a zero-knowledge validity proof that mathematically confirms its correctness before it’s ever written to the main chain. This provides immediate finality and stronger security guarantees, albeit with greater technical complexity and heavier computation requirements.
In essence, the two models represent different trade-offs. Optimistic rollups are easier to implement and currently dominate Ethereum’s Layer-2 landscape due to their simplicity and full EVM compatibility. ZK rollups are more complex and computationally demanding, but they offer faster settlement, lower costs, and the potential for built-in privacy.
Conclusion
Zero-knowledge proofs represent a paradigm shift in how we think about trust, privacy, and verification in digital systems. What began as an abstract cryptographic theory in the 1980s has become one of the most promising technologies driving the next generation of decentralized infrastructure.
In crypto, ZK proofs power private transactions, decentralized identity, cross-chain interoperability, and, most notably, scalable rollup architectures that preserve Ethereum-level security while multiplying throughput. Their applications extend beyond blockchain too, into finance, AI, and data verification.
While application of ZK proofs remains relatively nascent, its trajectory is clear. Zero-knowledge proofs are moving from cryptographic novelty to infrastructural necessity. If blockchains are to scale to billions of users while preserving privacy and decentralization, zero-knowledge may well be the key that unlocks that future.









































































































































































































































































































.png)