February 22, 2025
at
12:00 am
EST
MIN READ
Bybit Exploited for $1.4B

Centralized exchange, Bybit, sees suspicious outflows of $1.5B worth of ETH, Lido Staked ETH (stETH), and Mantle’s mETH and cmETH tokens, after their ETH cold wallet was exploited. A total of 401K ETH, 90.4K stETH, 8,000 mETH and 15,000 cmETH were transferred out to the hacker, 0x476. The hacker then began transferring the tokens out to more than 40 fresh addresses, with stETH tokens sold off for ETH.
The compromise of a cold wallet is particularly alarming within the crypto industry. These wallets are, by design, kept offline to secure funds from the exact type of online threats that lead to exploits, implying a severe breach of operational security.
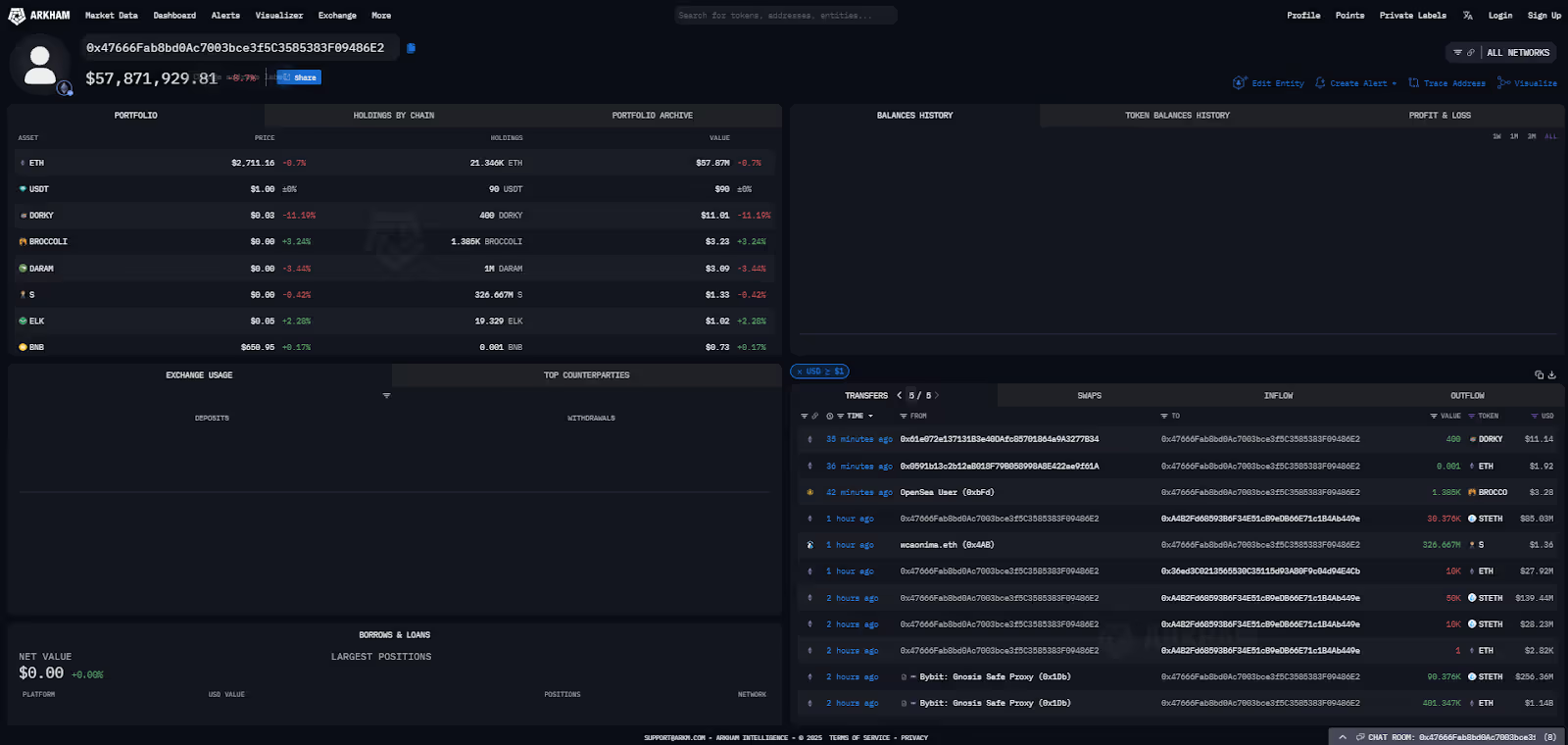
The attacker's immediate distribution of funds across dozens of new addresses is a classic tactic. This method is used to obscure the flow of the stolen assets, making it significantly more difficult for the exchange and law enforcement to trace, freeze, or recover the funds.
In the official statement put out by Bybit CEO, Ben Zhou, attributes the exploit to the signing of a fraudulent transaction via a phishing attack during a scheduled cold wallet migration. Fortunately, only the ETH cold wallet is affected and all other wallets remain secure. That said, users have reported delays in withdrawals from the exchange, especially on EVM networks.
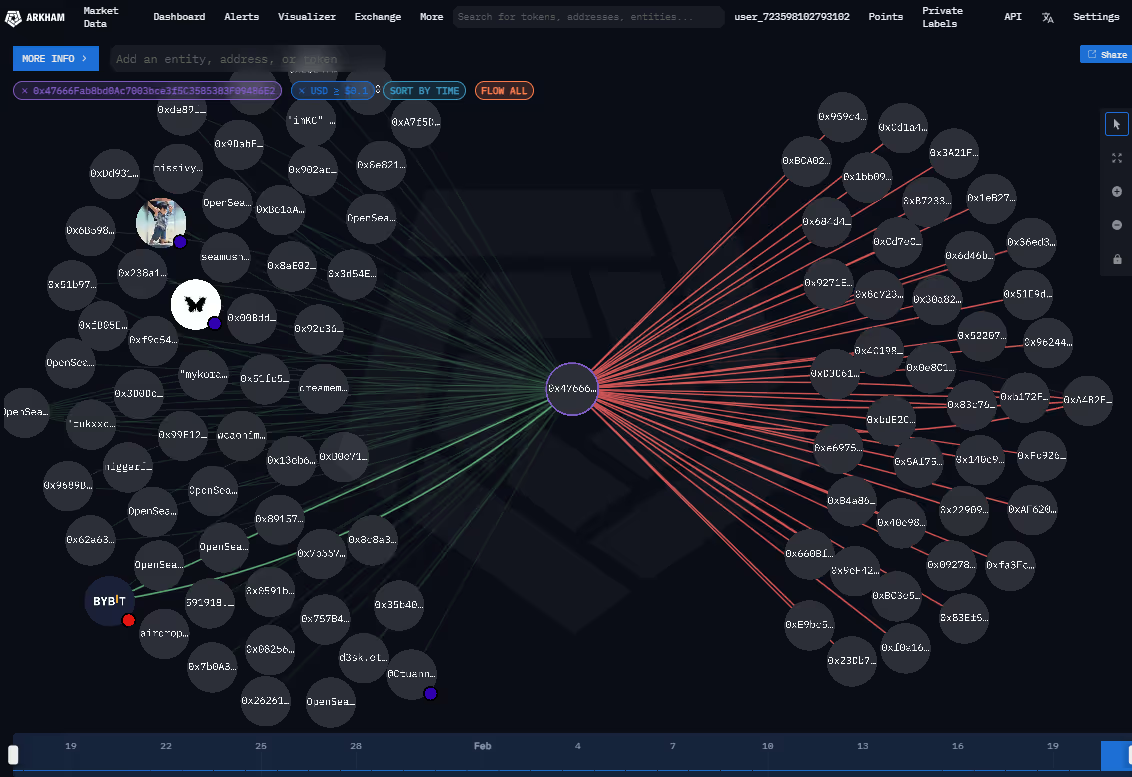
Pinpointing the cause to a phishing attack underscores a critical vulnerability in crypto operations: the human element. Sensitive procedures like wallet migrations are high-stakes moments, often targeted by attackers hoping to exploit human error.
he user-reported withdrawal delays, even on supposedly secure wallets, are a common consequence of such an event. Exchanges will often heighten security protocols and manually review transactions post-breach to prevent further losses, leading to a temporary slowdown of services.

.png)

.png)































.webp)

.webp)














































































































































.avif)

.avif)
























.avif)

.avif)

































































.avif)

.avif)




















.png)




.webp)